What is IEC 62443 standards?
IEC 62443 is a series of international standards developed by the International Electrotechnical Commission (IEC) for industrial automation and control systems (IACS) security. The standards provide a comprehensive framework for protecting IACS systems and networks from cyber threats, and are designed to help organizations establish and maintain effective cybersecurity practices.
Why IEC 62443?
The consequences of a successful cyberattack on an Industrial Automation and Control System (IACS) is fundamentally different from those against a traditional IT system and can lead to loss of life or significant damage to the environment. The International Society of Automation (ISA) and the International Electrotechnical Commission (IEC) have joined forces to address the need to improve the cybersecurity of IACS by publishing the ISA/IEC 62443 series. The main concepts promoted by the standards are that first, cybersecurity is an ongoing process and not a goal that can be reached. Second, security-by-design require defense in depth through layering multiple protective solutions. And third, ICS components need to be separated into zones based on security requirements and communications among zones need to go through well-defined conduits. NP-View has been designed by ICS experts to easily and independently visualize network zones and to verify inbound and outbound network conduits connectivity.
Foundational Requirements
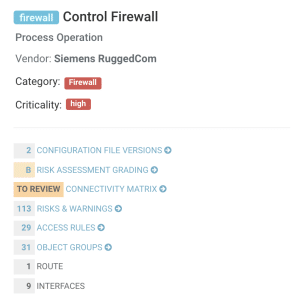
NP-View ingests the configuration files of OT firewalls, routers, and layer-3 switches to automatically generate a comprehensive topology map of your ICS environment. The modeling engine computes all possible data flows in order to verify compliance with the following requirements:
IEC 62443 part 3-2: Security risk assessment for system design
- ZCR 3: Partition the SUC into zones and conduits
- ZCR 3.1: Establish zones and conduits.
- ZCR 3.2: Separate business and IACS assets.
- ZCR 3.3: Separate safety related assets.
- ZCR 3.4: Separate temporarily connected devices.
- ZCR 3.6: Separate devices connected via external networks.
- ZCR 6: Document cyber security requirements, assumptions and constraints
- ZCR 6.3: Zone and conduit drawings.
- ZCR 6.4: Zone and conduit characteristics.
IEC 62443 part 3-3: System security requirements and security levels
- FR 5 – Restricted data flow
- SR 5.1: Network segmentation.
- SR 5.2: Zone boundary protection.
IEC 62443 part 4-2: Technical security requirement for IACS components
- FR 5 – Restricted data flow
- CR 5.1: Network segmentation.
- CR 5.2: Zone boundary protection.
How to comply with IEC 62443?
“The IEC 62443 standards consist of multiple parts, each addressing a different aspect of IACS security. The standards cover topics such as:
- Security management: This includes establishing a security management system, developing security policies and procedures, and conducting risk assessments.
- Security controls: This includes implementing technical and procedural controls, such as access controls, encryption, network segmentation, and incident response planning.
- System and network architecture: This includes designing secure architectures for IACS systems and networks, incorporating security into the design process, and managing security during the system lifecycle.
- System and network testing: This includes testing IACS systems and networks for vulnerabilities and weaknesses, and verifying that security controls are effective.
- Maintenance and patch management: This includes managing software and firmware updates, conducting vulnerability assessments, and ensuring that security controls are maintained over time.”
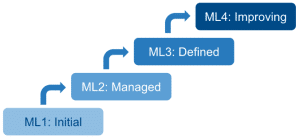
Where is your Maturity Level?
The team at Network Perception will provide you with the expertise, technology, and know-how to mature your ICS network cybersecurity program from initial to improving. Step-by-step, NP-View provides the ease-of-use and independent verification needed to ensure that best practices are managed, documented, and continuously improved. In addition, the platform provides risk assessment grading, actionable reports, and dashboard to precisely measure your progress and validate the effectiveness of your internal controls over time.
Ready to Get Started?
NP-View assesses your network’s security to ensure that misconfigurations and vulnerabilities are instantly identified and send you instant alerts when the network changes.