Change Management
Change Management provides the Compliance Team (Compliance Officer, Compliance Analysts) with capabilities that allow for:
- Transitioning from point-in-time risk assessment to 24/7 with automated notification.
- Automating the change review process using ticketing system integration and sandboxing.
- Leveraging “time machine” to navigate through the network evolution and compare points in time.
Transition to 24×7 Monitoring
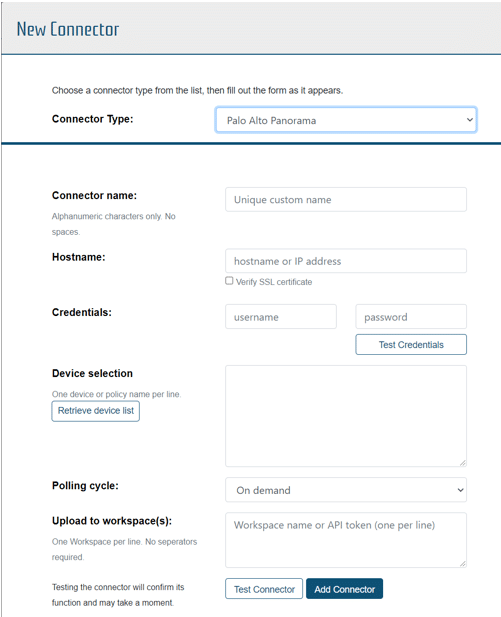
Connectors facilitate the configuration of connections to poll devices on a schedule, importing the latest configurations for analysis and automatically analyzing the information within selected workspaces to identify changes and potential risks.
Automated change review process
Change tracking automatically records configuration changes and provides the user with the ability to review changes made to the system and review the potential impact of the changes.
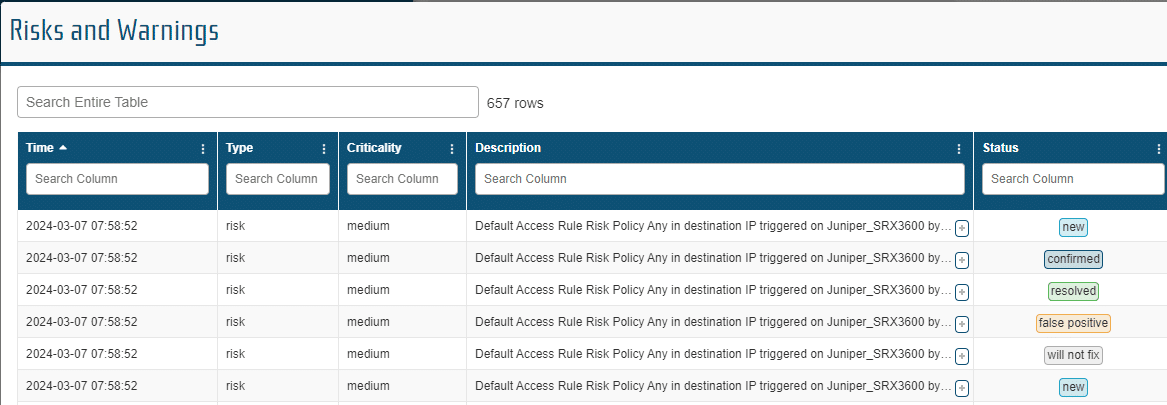
Network risks related to configuration changes are identified by best practices and user defined rules in the Policy manager. When a potential risk is identified, it is logged in the “Risks and Warnings” table and assigned a criticality (High, Medium, Low) based on the identifying policy.
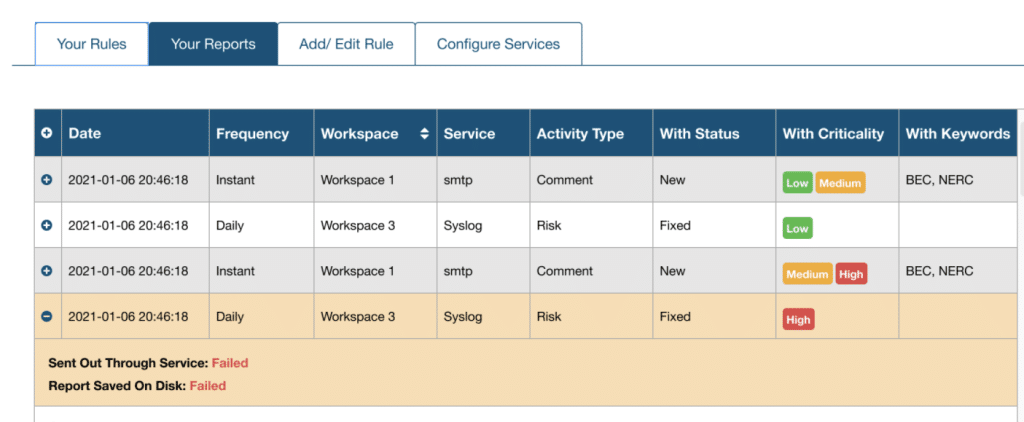
Notifications allow users to setup notifications based on complex rules and to have those notifications delivered to multiple services on a schedule to email, syslog or ticketing systems. Notifications can be triggered by configuration changes or network risks.
The Network Sandbox is an isolated workspace that aids network engineers and infrastructure managers with the evaluation of proposed changes to system configurations, operating system upgrades or hardware replacement without affecting the production network. Our network modeling platform provides the ability to evaluate proposed changes to network devices by importing modified configuration files, evaluating the changes against policies, best practices, and regulations, and reporting on risks and vulnerabilities. Additionally, changes can be reviewed and compared, paths and connectivity can be analyzed, compliance reports can be run and reviewed.
Comparison Analysis
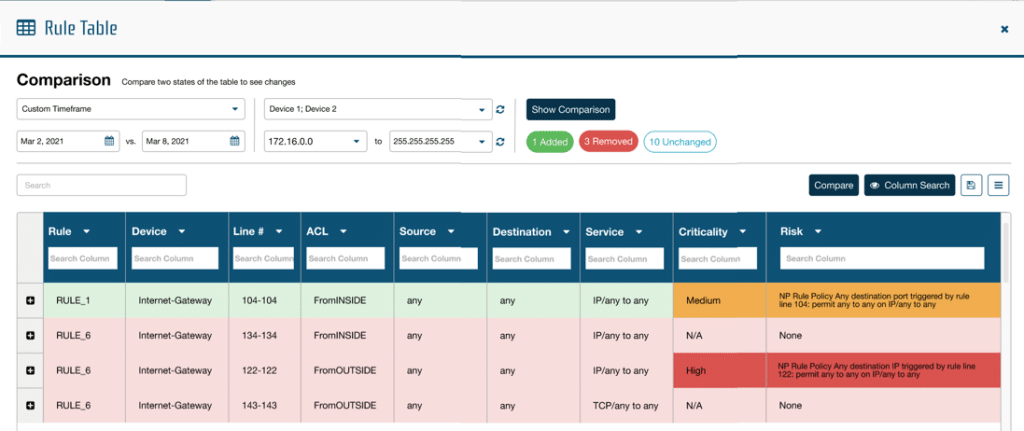
Tracking changes over time provides a rich data source for analysis. Comparison Analysis allows the user to review two points in time to identify changes across the system including assets, rules, objects, and paths.