Importing and Exporting Data
NP View supports several different methods of importing a variety of both primary device data, such as firewall configurations, and auxiliary data, such as hostname files.
Note: The Windows API has a maximum path length of 256 characters. When importing files into NP-View with long file names (typically > 50 characters), they may fail to import. Reducing the length of the file name before importing tends to resolve this issue.
Importing Primary Data
Once a workspace is created, the user can begin importing configuration files from Firewalls, Routers and Switches.
Import can be done by:
- Dragging and dropping files onto the Topology Map area
- Manually – Selecting Import from the top of the main menu and then selecting Manual Import
- Automatically – NP-View can also be configured to automatically retrieve files from devices, network management systems and file shares on a schedule. See the Connectors section for more information.
Multiple supported configuration files can be loaded at one time.
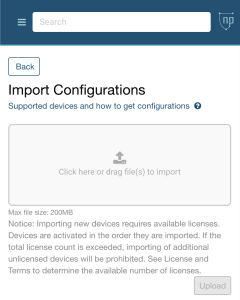
Manual Import

- Open the Main Menu
- Select Import Data
- Select Manual Import
- Add files to the Import Box
- Once the files are selected – review the files for accuracy, clicking ‘x’ on each file to remove and then clicking the Upload button to begin.
Import can take some time depending on the number and size of the files imported. The import status will be displayed on the import menu by a loading bar and by the background task spinner next to your user name in the upper right corner of the map. Upon completion of Import, the Home View of the Topology Map will be displayed.
—–
Note: Files from supported Network management Systems can also be imported. When this is the case, once the Upload is selected, a list of devices included in your files will be provided for selection. Only the selected devices will be imported.
Note: Device licenses are applied on First import. As files are loaded, the available license count goes down and the device is tracked across all workspaces. See the licensing section for more details.
Device Identification
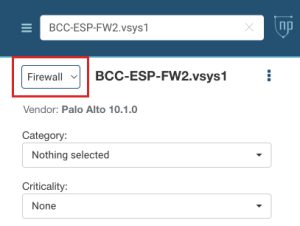
When you importing a device, NP-View uses a built-in device classifier to figure out what kind of device it is using device heuristics. However, because many devices can use the same configuration file, this can be tricky. For example, different Cisco hardware can run the same Cisco IOS, but the configuration file doesn’t tell you which hardware it is.
The device classifier tries to distinguish between routers and firewalls by looking for syntax differences like how static routes are expressed. But this isn’t always accurate since routers can use dynamic routing instead of static routes.
By convention, the NP-View device classifier will classify a device as a firewall if the configuration contains access lists. If the app misclassifies a device, the user can change the device type using the info panel for that device.
Importing Auxiliary Data
This table lays out the various types of Auxiliary Data NP-View accepts, and the order in which they should be prioritized for import. Primary Devices are considered Priority 1.
Once the relevant configuration files (priority 1) are loaded, auxiliary data may be added to a workspace to enrich and augment the analysis and topology visibility.
Each workspace can only handle one file of each auxiliary type at a time. This was done to support change tracking of hosts on the network. When a new file is uploaded, it completely overwrites the older file of that type regardless of the creation date of the file.
As multiple files can have similar data, we have implemented a data priority to facilitate data enrichment and prioritization of data importance within the system.
| Priority | File Types | Content |
| 2 | Scanner: nmap, nessus, nexpose | CVE info (ID, severity, Exploitability, Remediation suggestion) |
| 3 | Scanner: nmap, nessus, nexpose | Host Discovery (IP, HW Address, status), OS and Services |
| 4 | netstat | Host Discovery (IP, status), OS and Services |
| 5 | ARP | MAC Address, Host |
| 6 | hosts (user created) | Text (IP / Hostname) |
Please see the auxiliary data section for information on file types and structures for the file types.
Export Workspace Data
NP View allows for several different methods of exporting different types of workspace data.
Export Comments and Metadata
The entire Access Rules and Object Groups table and its contents can be exported to an Excel formatted document. The export will only contain the visible columns in the report.
It is important to keep the comments columns (Comment, Comment Author, Comment Status) as well as the Object Id column visible as they are required for subsequent import.
It is recommended that at least one row of data be manually filled in with metadata before export to fully populate the template with examples of the field format.
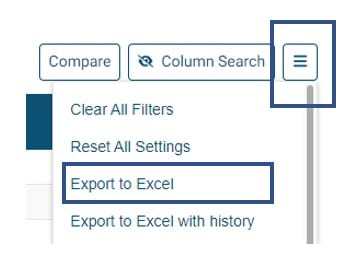
For Access Rules, there are three export options:
- Export to Excel – Exports visible cells to an excel file (.xlxs)
- Export to Excel with history – Exports visible cells to an excel file with comment history.
- Export to Excel with expanded objects – Exports visible cells to an excel file with expanded object groups and objects.
For Object Groups, there are two export options:
- Export to Excel – Exports visible cells to an excel file (.xlxs)
- Export to Excel with history – Exports visible cells to an excel file with comment history.
Once the export button is clicked, the file (rule.xlsx, or object.xlsx) will automatically download. The file will contain all of the visible table columns plus multiple columns of comment data.
Enriching Metadata
As part of the audit process, Comments can be updated for Access Rules and Object groups as discussed here. Once the primary and secondary data is loaded, the user may want to bulk load justification data into the Access Rules and Object Groups tables.
Access Rules
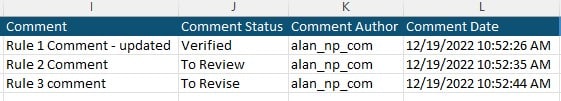
The access rules export will contain four columns of data for each comment as below.
- Comment field contains the user entered text. If cleared or left blank, the comment will be updated accordingly.
- Comment Status choices are ‘Verified’, ‘To Revise’, ‘To Review’ or can be left blank.
- The Comment Author field contains the user who entered the last change. Upon import, this field will be automatically populated with the userid of the importer. Manual inputs into this field will be ignored.
- The Comment Date field contains the date of last change. Upon import, this field will be automatically populated with the current date if a change has been detected. Manual inputs into this field will be ignored
Object Groups
The Object groups export works the same as the Access rules except the Comment Criticality column will accept ‘Low’, ‘Medium’, ‘High’ or can be left blank.
Importing Metadata
Once the file is updated and saved, the user can use the +Import function or simply drag and drop the file into the workspace for upload.
Only metadata fields that have been added or changed will be imported. A time stamp and username of the importer will be applied when imported. The results will be viewable in the report after processing is complete and the report has been refreshed. Updates to comment and metadata history, standard NP-View fields and expanded objects will be ignored upon import.
Note that the import keys on multiple fields to match data. The following fields are required in the file to properly import.
- Object ID
- Comment
- Comment Status
- Comment Author
Importing Legacy NP-View Gen 1 Data
NP-View Gen I Project Import
Both Administrators and Workspace Admin’s can import a previously saved project file from NP-View Gen I (Java).
- The user can drag and drop the project file on to the workspace page or into an open workspace.
- If the user loads a project file into an existing workspace, the workspace contents will be replaced with the contents of the project file.
- If the user loads the project file onto the workspaces page, it will be processed as if it is a new workspace and request name and compliance type.
- When a project file is imported, complete end-to-end processing of the data is required and may take several minutes for the topology to render.
- The topology, zones and comments from a NP-View Gen I project will be imported into NP-View.
- Workspaces exported from NP-View cannot be opened in NP-View Gen I.
Tip: One or more saved workspaces or NP-View Gen I projects can be dropped onto the workspaces page. A new workspace will be created with the name of the file and the information loaded into the new workspace.