What is Cyber Resiliency, and why is it important?

| TL;DR: Cyber Resiliency for Utilities |
|
The State of Cyber Security in 2021
Our dependence on cyber systems is increasing every day and the frequency, severity, and sophistication of cyber attacks has been rising along with it. The size and complexity of networks have also grown exponentially, continuously exposing organizations to larger attack surfaces. As a result, companies are investing in cyber security solutions to keep the latest malware outside of their infrastructure. As shown by the recent Solarwinds breach, cyber security monitoring solutions themselves can become an attack vector and, as experienced by the 18,000 customers affected, cleaning up after the breach is an extremely stressful endeavor.
What Is Cyber Resiliency
The goal of eliminating all cyber threats is futile since organizations will continue to depend on cyber systems and attackers will keep targeting them. To succeed in overcoming this arms race requires investing in cyber resiliency. This means the ability to recover from, and adjust rapidly to cyber risks. Similar to the immune system, that has developed protection, detection, and evolution capabilities over hundreds of thousands of generations to keep organisms alive despite the constant assault from viruses and diseases, organizations have to embrace the principles of cyber resiliency to keep operating despite cyber threats.
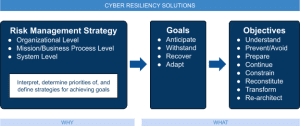
The National Institute of Standards and Technology (NIST) published the Special Publication 800-160 Volume 2 to present objectives, approaches, and techniques surrounding the development of cyber resilient systems. In particular, the following diagram represents the relationship among cyber resiliency constructs:
How to Achieve Cyber Resilience
With the intention of creating a cyber resilient organization, here are the first steps to take:
- Define a risk management strategy that will identify acceptable and unacceptable risks along with the resources allocated to mitigate them at the organizational, business process, and system levels.
- Prioritize goals and objectives according to the specificities of the organization, before being implemented through a set of techniques such as analytic monitoring, non-persistence, and privilege restriction.
The first objective of cyber resiliency is to understand. It is defined in the NIST publication as maintaining useful representations of mission and business dependencies and the status of resources with respect to possible adversity. Indeed, we cannot protect what we do not know and in the domain of information systems and networks, it is paramount for an organization to gain and maintain accurate visibility on their infrastructure: which assets are installed, how those assets are configured, and how access policies are effectively segmenting networks into distinct zones. It is also vital for first responders to not only maintain situational awareness but also to reduce the time between receipt of threat intelligence and determination of its relevance in order to adapt rapidly to adversarial conditions.
Helping You Build a Culture of Resilience
In this blog post series, we will present cyber resiliency techniques that can be applied to networks and access policies. Our goal is to provide practical advice to:
- Security teams can adopt key techniques to build cyber resilience over time,
- Compliance teams can assess and track progress to help guide their organizations, and
- The utility industry can better understand the importance of, and how to build a more cyber resilient organization.