Configuring Connectors (Server)
Connectors automate the secure retrieval of configuration files from firewalls, routers, switches, and network device configuration managers. NP-View Server can host one or more connectors that securely retrieves configuration files at the specified frequency. By default, connectors are accessible through HTTPS on port TCP/8443 of the NP-View server and is isolated for security purposes.
The first time an administrator accesses the connectors (+Import Data -> New connector -> Manage connectors), they are required to define a Connector group name and a secure passphrase. The Connector group name will be used to create the encrypted connector file store. Connector information is encrypted at rest and in transit using a passphrase protected PGP key. Only the connector owners know the passphrase and the passphrase is never stored. Once initiated, connectors run in the background collecting network information. If the NP-View server is restarted, the connector owner is required to re-authenticate and restart the connectors. Connector owners can create multiple connector groups and each will require their own login. Once created, the user can select from the list of available connectors when logging in.
The connector page contains five main options.
The buttons from left to right are:
- + Add New Connector
- bulk start all connectors (see bulk start parameters below)
- bulk stop all connectors
- delete the connector (user must be logged into the connector group to delete)
- exit the connector group.
Add Connector
To add a new connector, select “+Add New Connector” button and a list of available connectors is presented. Connector options are: Cloud Providers, Configuration Managers, Direct Devices and Volume Shares
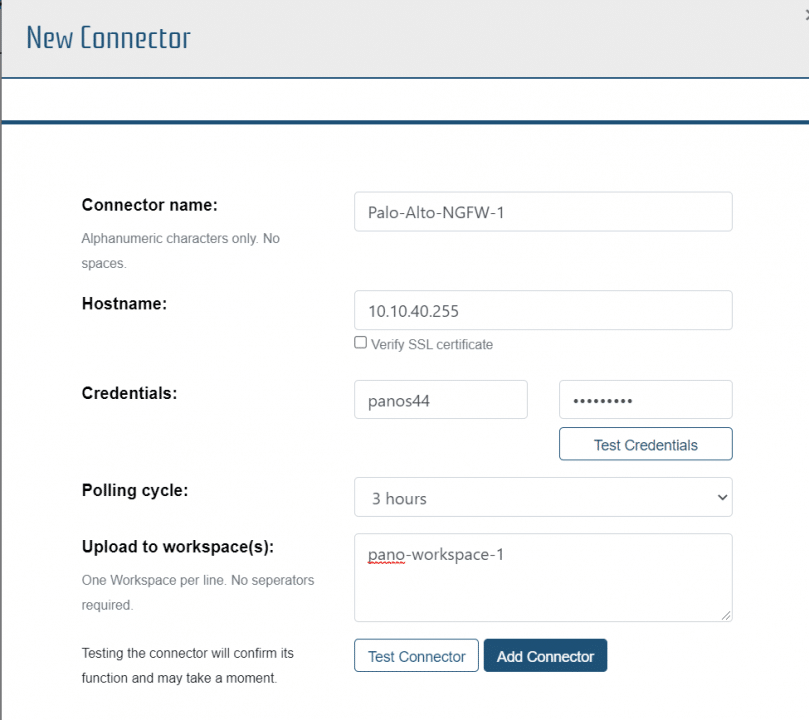
Upon selecting the Connector type to add, the user is requested to fill in connection information. Connector information varies by vendor. The connector configuration for a Palo Alto device is as follows:
The user must enter a Connector name (no spaces), host name, and credentials. The user can then verify the credentials are correct with the “Test credentials” button. The user can setup the polling cycle and provide the workspaces to deliver the resultant information.
Polling Cycles are:
- On demand
- Daily
- Weekly
- Bi-Weekly
- Monthly
Configuration Management Systems
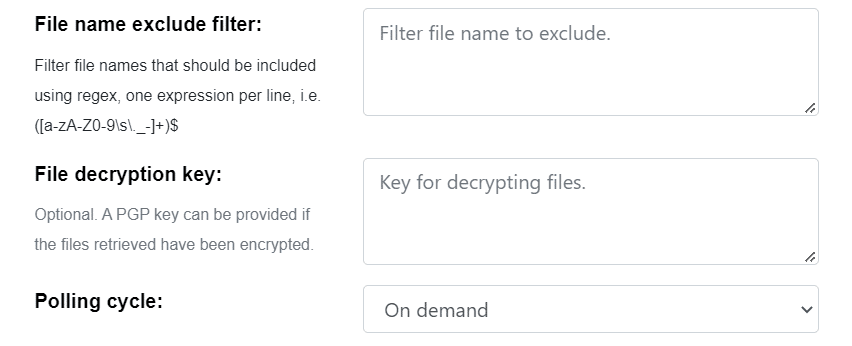
For Configuration Management Systems and file Shares, additional information may be required. The user can retrieve a list of files from the device and filter the results. To include specific files, put them in the include list field. To exclude files, put them in the exclude list field. If both lists are used, include list filter will be applied first and the exclude list filter to the results of the include list filter. If the share is PGP encrypted, a PGP Public key will be required.
Workspaces must be added to the connector for data to be transferred and displayed in the workspace. If workspaces are added after a connector is setup, data will not be sent to the workspace until the next scheduled import and a configuration change is identified. Creating workspaces before connectors facilitates faster visualization of data.
Connector Tile
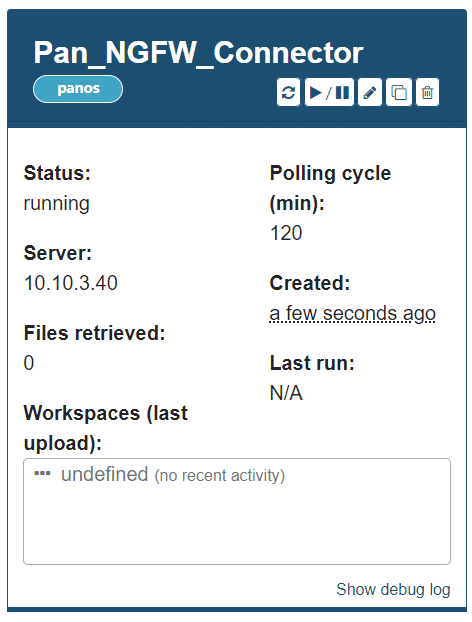
Once the connector is added, a tile is added to the connectors home page.
Connector tiles are sorted by the characters in their names using standard Linux conventions:
- whitespace
- integer
- special char
- uppercase [A-Z]
- underscore (possibly other special chars)
- lowercase [a-z]
From the tile, the user can:
- manually activate the connector for a one time data pull
- run / pause the connector
- edit the connector
- copy the connector
- delete the connector.
The tile banner will show in three colors:
- red – connector failed
- blue – connector scheduled to run
- gray – connector paused
Click the start / pause button to restart a failed or paused connector, note that a connector may take several minutes to change the banner color.
Connector for Forescout
The Connector for Forescout 8.1 and later enables integration between CounterACT and NP-View such that network device configuration files managed by CounterACT can be automatically imported into NP-View and aggregated into specific workspaces. Currently, Cisco switches are supported through the Forescout Switch Plugin.
- Download the Forescout Extended Module for NP-Vie from https://updates.forescout.com.
- Start your Forescout Console and login into Enterprise Manager.
- Then open “Options”, select “Modules”, and install the fpi.
To request additional support for this connector or to request support for other devices, please contact support@network-perception.com.
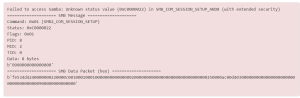
Connectors + Samba (SMB) Access Error
When connecting a connector to a Windows Server using SMB, an error message may occur.
This error can be caused by two communication scenarios between Linux and Window. Either SMB encryption is enabled on the Server or SPN target name validation level is enabled (or both). To check which of these features is causing the issue, Run PowerShell on the Windows Server as administrator and run the following command:
Get-SmbServerConfiguration
If EncryptData = True, it can be disabled using:
Set-SmbServerConfiguration -EncryptData 0
If SmbServerNameHardeningLevel is set to any value other than the default of 0 run:
Set-SmbServerConfiguration -SmbServerNameHardeningLevel 0
to restore the default.
Connectors fails to initiate connection to outside devices
In some instances, the Linux distribution is preventing the connectors (Docker) from initiating connections to outside devices. The solution is to update the firewall settings on the Linux distribution using the following commands:
# firewall-cmd --zone=public --add-masquerade --permanent # firewall-cmd --reload # systemctl restart docker
Configuring Read-only Access to Cisco
The NP-View Connector for Cisco uses a read-only SSH connection to collect the output of the show running-config command. It is best practice to create a dedicated read-only user on your Cisco devices when configuring connectors. Here are the commands to only give the minimum permissions needed for this user:
conf t aaa authorization command LOCAL privilege show level 2 mode exec command running-config privilege cmd level 2 mode exec command terminal username $USERNAME password $PASSWORD priv 2 end
Bulks Start Parameters
To help balance the processing load of managing multiple connectors and improve user experience on the topology map, the bulk start function can be scheduled to off hours using system parameters. The docker-compose.yml file contains two parameters for the bulk system start function in the monitor: environment: section
connBulkStartTime=21:00:00# defines the start time for the connectors, format is Hours:Minutes:Seconds, 24 hour clock.connBulkStartSpread=00:15:00# defines the connector start stagger, format is Hours:Minutes:Seconds
Deleting Connectors
Connectors can be deleted by entering the connector group name and passphrase to gain access to the connector. The connector can be deleted by selecting the trash can in the upper right corner.
If the passphrase is forgotten, the connector can be forcefully deleted by the Linux Admin by removing the connector file from the folder
/var/lib/docker/volumes/NP-Live_np-connect/_data.